Hardware Hacking Bootcamp
Hack, extract, and attack through signal and protocol analysis
Course Information
- Course Name: Hardware Hacking Bootcamp
- Duration: Five Days
- Cost Per Student: $3500
- Syllabus / Additional Information: Detailed Syllabus and Price Sheet
Course Overview and Information
This five-day course is designed to teach the fundamentals of hardware reverse engineering and analysis. With a focus on understanding the low-level protocols that make up embedded systems, students learn how interfaces such as SPI, I2C, JTAG, SWD work while developing tools to interface with these protocols. All hardware is provided for this course, and all tools are kept by the students upon completion of the course.
This blog post provides an overview of what to expect from an onsite offering. Additional details can be found below.
Course Objectives
After participating in this course, students will have experience with:
- Non-Invasive hardware analysis (component identification, etc)
- Tracing and identifying points of interest on PCBs
- Extracting firmware over multiple interfaces
- Unpacking / analyzing binary images
- Attacking/instrumenting hardware debuggers (JTAG,ETC)
- Modifying, repacking and reflashing firmware
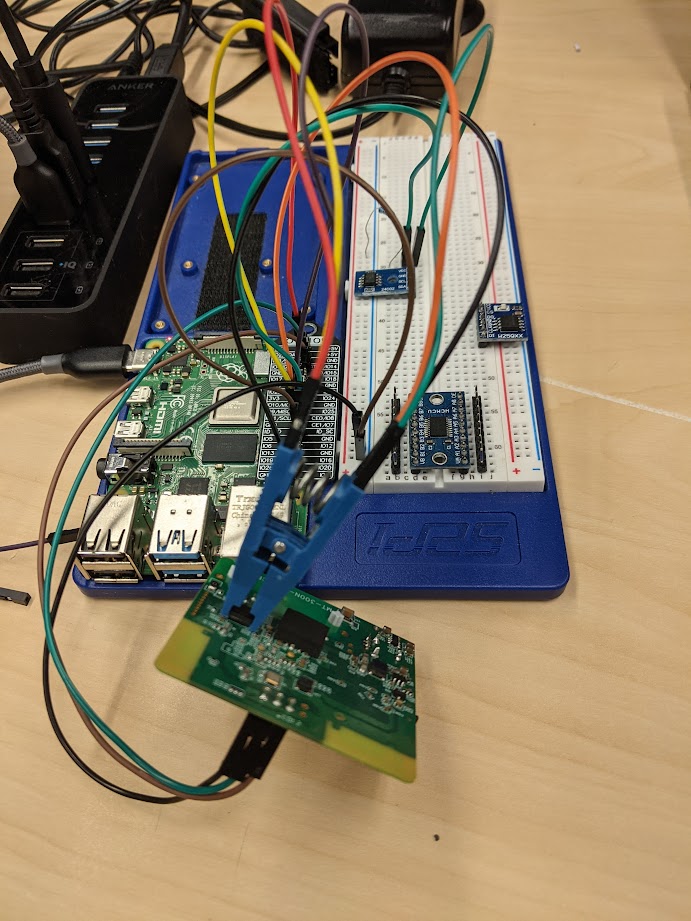
Labs include extracting SPI/I2C-based flash chips, discovering and gaining access to consoles using UART, and identifying, enumerating, and actuating hardware-level debuggers such as JTAG and SWD. Labs are performed on four different real-world targets after introductory protocol labs are performed. Each target was chosen in order to demonstrate a specific protocol, allowing students to gain experience across multiple hardware platforms throughout the course.
All exercises and laboratories are performed using open-source tooling on a Raspberry Pi. The Raspberry Pi will be used to attack and exploit all of the targets included in the kit. The tools and techniques used throughout the course were chosen specifically due to their portability across various hardware platforms.
Course Structure
This course includes multiple modules, one for each protocol of interest. For each module, we will perform the following:
- Protocol Overview and Analysis
- Understanding and Reviewing Captured Protocol Traffic
- Protocol Analysis from a Reverse Engineering Perspective
- Tools for Reverse Engineering Specific Protocols
- Practical Attacks and Applications on Provided Targets
Course Modules
Hardware Targets
Students will receive a hardware kit including:
- Raspberry Pi 4 with USBC cable and power supply
- Target #1: Travel Router
- Target #2: Arcade Cabinet
- Target #3: ARM Based USB Controller
- Target #4: Solid State Drive + USB Adapter
- Breadboard, logic level shifter, jumper wires
- Multimeter
- Logic Analyzer
- SOIC8 Clip
- SPI EEPROM, I2C EEPROM

Requirements
This course is targeted toward security researchers who want to learn more about the process of firmware extraction and embedded systems analysis. Students should be familiar with the Linux command line and be comfortable with a scripting language such as python. C experience is also useful but not required
Interfacing with the Raspberry Pi requires an available USB port. A virtual machine is also provided to automate the configuration of the Raspberry Pi. Students should be able to load and run virtual machines if they are not comfortable installing Pulseview and configuring an ethernet interface on their host machine.